HiddenServices 2019-12-15, PDF, Computing
Por um escritor misterioso
Last updated 23 setembro 2024


Navigate eBook Access for Hacker Techniques, Tools, and Incident Handling with Cloud Labs: 9781284172614

PDF) Protecting against Website Fingerprinting with Multihoming
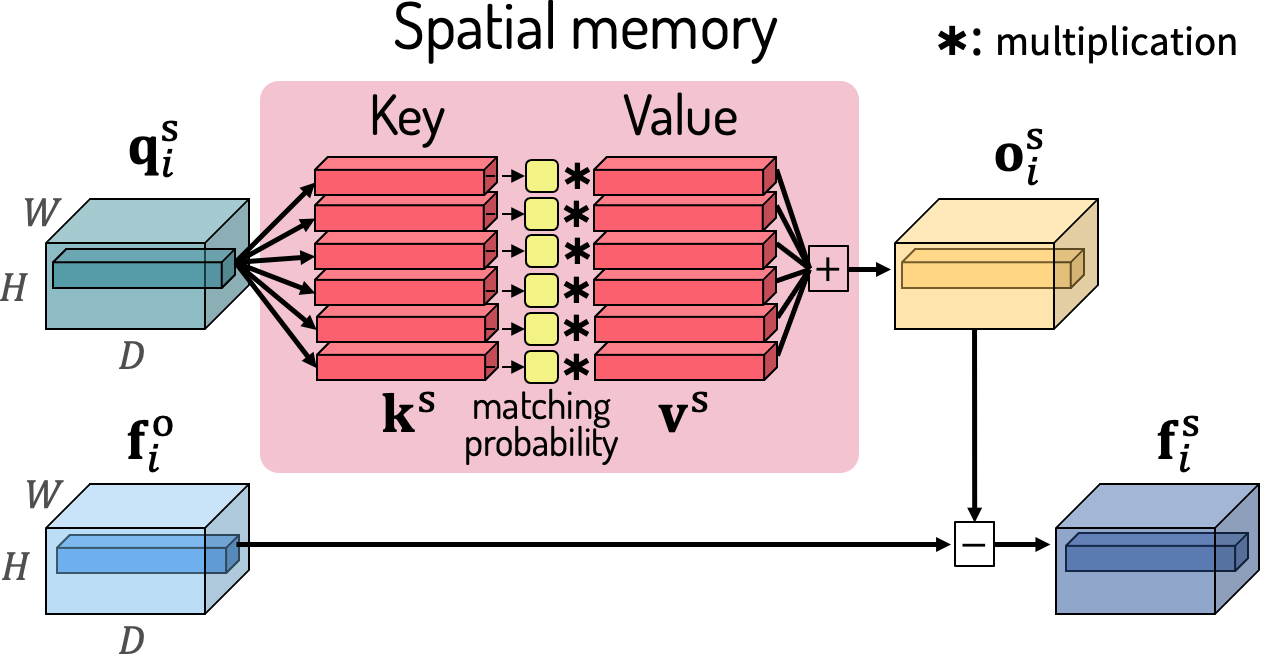
Video-based Person Re-identification with Spatial and Temporal Memory Networks
(ICCV 2021)

PDF) Protecting against Website Fingerprinting with Multihoming

PDF] Content and Popularity Analysis of Tor Hidden Services

Embedding and Hiding Files in PDF Documents

DMM Help: Submitting Text-Searchable PDFs
Code: The Hidden Language of Computer Hardware and Software HD PDF

HiddenServices 2020-1-8, PDF

PDF) Tor Network Architecture, Anonymity and Hidden Services

YO19 AC CH03 GRADER PC2 HW Instructions.docx - Grader - Instructions Access 2019 Project YO19 Access Ch03 Prepare - Turquoise Oasis Spa Data Management

heartbeat-step-11-templates-for-engine-nodes.jpg

PDF) Protecting against Website Fingerprinting with Multihoming

High-capacity reversible data hiding in encrypted image based on Huffman coding and differences of high nibbles of pixels - ScienceDirect
Recomendado para você
-
 8chan returns to the internet as 8kun - The Verge23 setembro 2024
8chan returns to the internet as 8kun - The Verge23 setembro 2024 -
 8chan – Wikipédia, a enciclopédia livre23 setembro 2024
8chan – Wikipédia, a enciclopédia livre23 setembro 2024 -
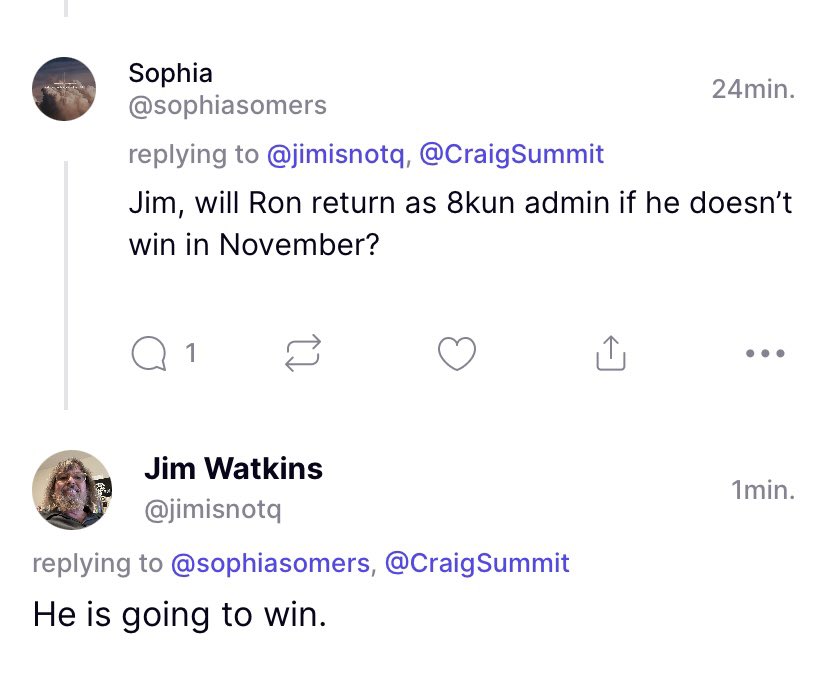 𝟚𝟘𝟚𝟛 𝕂𝕒𝕣𝕞𝕒 🌻🌻 a X: Jim Watkins was just asked if Ron will return as an Admin on 8kun, if he doesn't win in November. Jim respond with “He is going to23 setembro 2024
𝟚𝟘𝟚𝟛 𝕂𝕒𝕣𝕞𝕒 🌻🌻 a X: Jim Watkins was just asked if Ron will return as an Admin on 8kun, if he doesn't win in November. Jim respond with “He is going to23 setembro 2024 -
 8chan vuelve a estar en línea como 8kun - Novedades Tecnología - Tecnología23 setembro 2024
8chan vuelve a estar en línea como 8kun - Novedades Tecnología - Tecnología23 setembro 2024 -
 QAnon, a nova teoria da conspiração que se prepara para entrar no Congresso dos EUA, Internacional23 setembro 2024
QAnon, a nova teoria da conspiração que se prepara para entrar no Congresso dos EUA, Internacional23 setembro 2024 -
 Como acessar o 4Chan : r/InternetBrasil23 setembro 2024
Como acessar o 4Chan : r/InternetBrasil23 setembro 2024 -
4chan Onion23 setembro 2024
-
 examen teorico florida|TikTok Search23 setembro 2024
examen teorico florida|TikTok Search23 setembro 2024 -
 provedores - Olhar Digital23 setembro 2024
provedores - Olhar Digital23 setembro 2024 -
HiddenServices 2020-1-13, PDF, Wide Area Network23 setembro 2024
você pode gostar
-
 15 Incredible Places to Visit in Armenia Plus, Stay, Eat, Play - The Armenian Mirror-Spectator23 setembro 2024
15 Incredible Places to Visit in Armenia Plus, Stay, Eat, Play - The Armenian Mirror-Spectator23 setembro 2024 -
 Xshum Adjustable Supination Insoles & Overpronation Insoles, Medial & Lateral Heel Cups for Foot Alignment, Knee Pain, Bow Legs, Osteoarthritis23 setembro 2024
Xshum Adjustable Supination Insoles & Overpronation Insoles, Medial & Lateral Heel Cups for Foot Alignment, Knee Pain, Bow Legs, Osteoarthritis23 setembro 2024 -
 Hedgehogs Can't Swim: Sonic: Night of the Werehog23 setembro 2024
Hedgehogs Can't Swim: Sonic: Night of the Werehog23 setembro 2024 -
 Who is Black Swan in Honkai Star Rail? Leaked abilities, trailer23 setembro 2024
Who is Black Swan in Honkai Star Rail? Leaked abilities, trailer23 setembro 2024 -
 Cheque De Xadrez Ou Xeque-mate Corta Figura O Conceito De Competição Nos Negócios Foto de Stock - Imagem de preto, luta: 18575702223 setembro 2024
Cheque De Xadrez Ou Xeque-mate Corta Figura O Conceito De Competição Nos Negócios Foto de Stock - Imagem de preto, luta: 18575702223 setembro 2024 -
 Sinto muito: criador Attack on Titan pede desculpas para estúdio23 setembro 2024
Sinto muito: criador Attack on Titan pede desculpas para estúdio23 setembro 2024 -
 Anime Kaze No Stigma HD Wallpaper23 setembro 2024
Anime Kaze No Stigma HD Wallpaper23 setembro 2024 -
.jpg) God Of War Ragnarök: What Makes Odin Kratos' Perfect Villain23 setembro 2024
God Of War Ragnarök: What Makes Odin Kratos' Perfect Villain23 setembro 2024 -
 How to install XBoX Series X Upgrade on DRAGON BALL Z: KAKAROT23 setembro 2024
How to install XBoX Series X Upgrade on DRAGON BALL Z: KAKAROT23 setembro 2024 -
 All Call of Duty Store Bundles Modern Warfare 2 (MW2)|Game823 setembro 2024
All Call of Duty Store Bundles Modern Warfare 2 (MW2)|Game823 setembro 2024
